Computer Vision over Homomorphically Encrypted Data
CVPR 2025 Tutorial
June 12, 2025
Progress In Artificial Intelligence
Speech Processing
Image Analysis
Natural Language Processing
Physical Sciences
State of Affairs
(report from the academic-world)Attacks on Face Recognition Systems
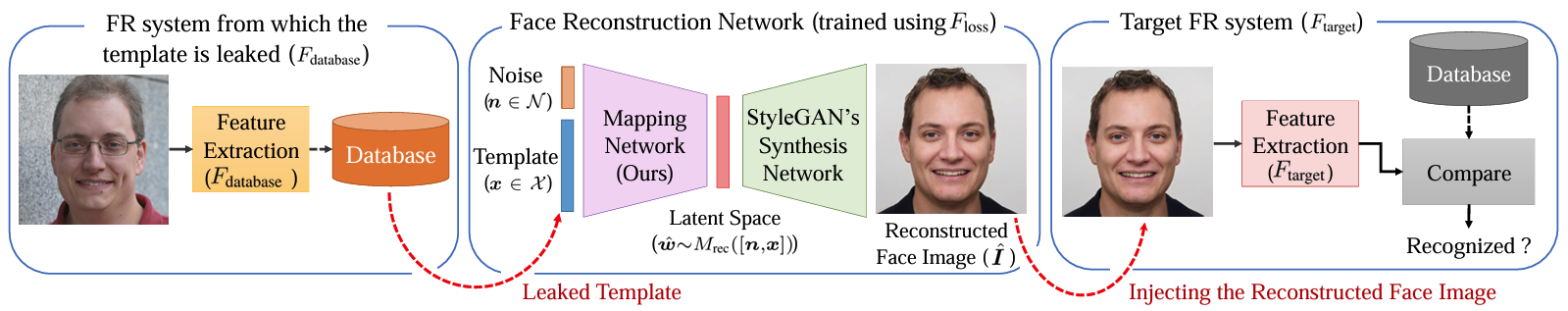
Attacks on Face Recognition Systems: Template Inversion


Template inversion attack on High resolution image
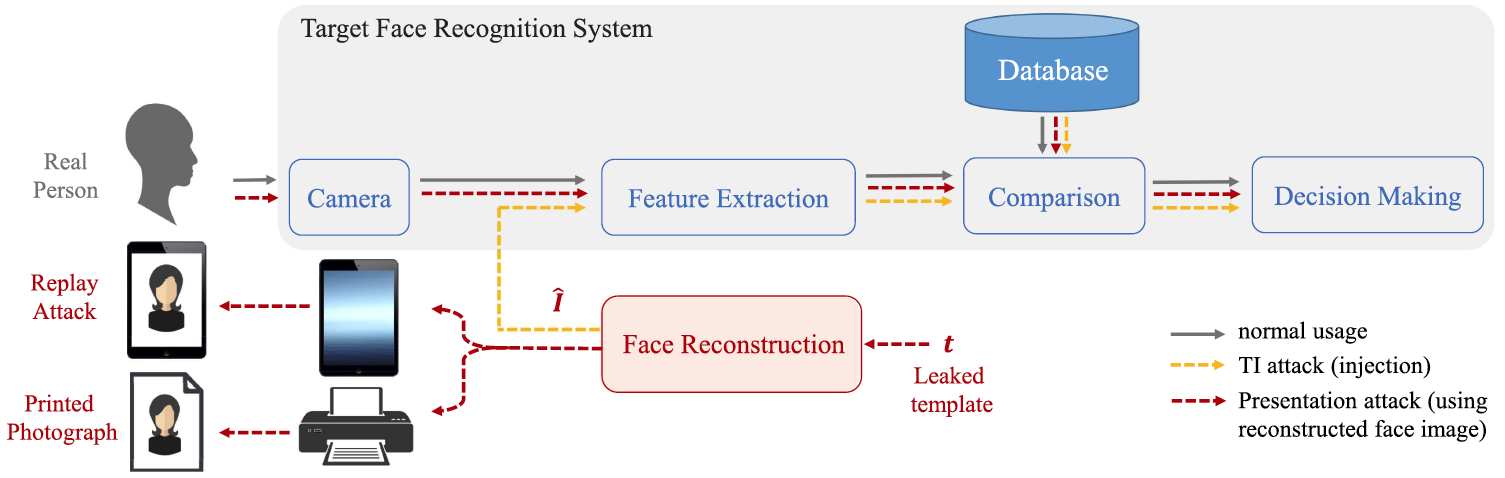
From Template inversion attack to Replay and Presentation attack

Template inversion attack enables Presentation attack
Presentation attack via digital replay and printed photograph


Attacks on Augmented Reality Systems
Privacy Leakage in Augmented Reality

- Pittaluga et. al., "Revealing Scenes by Inverting Structure from Motion Reconstructions", CVPR 2019
Attacks on Large Language Models
Attacks on Text Embeddings
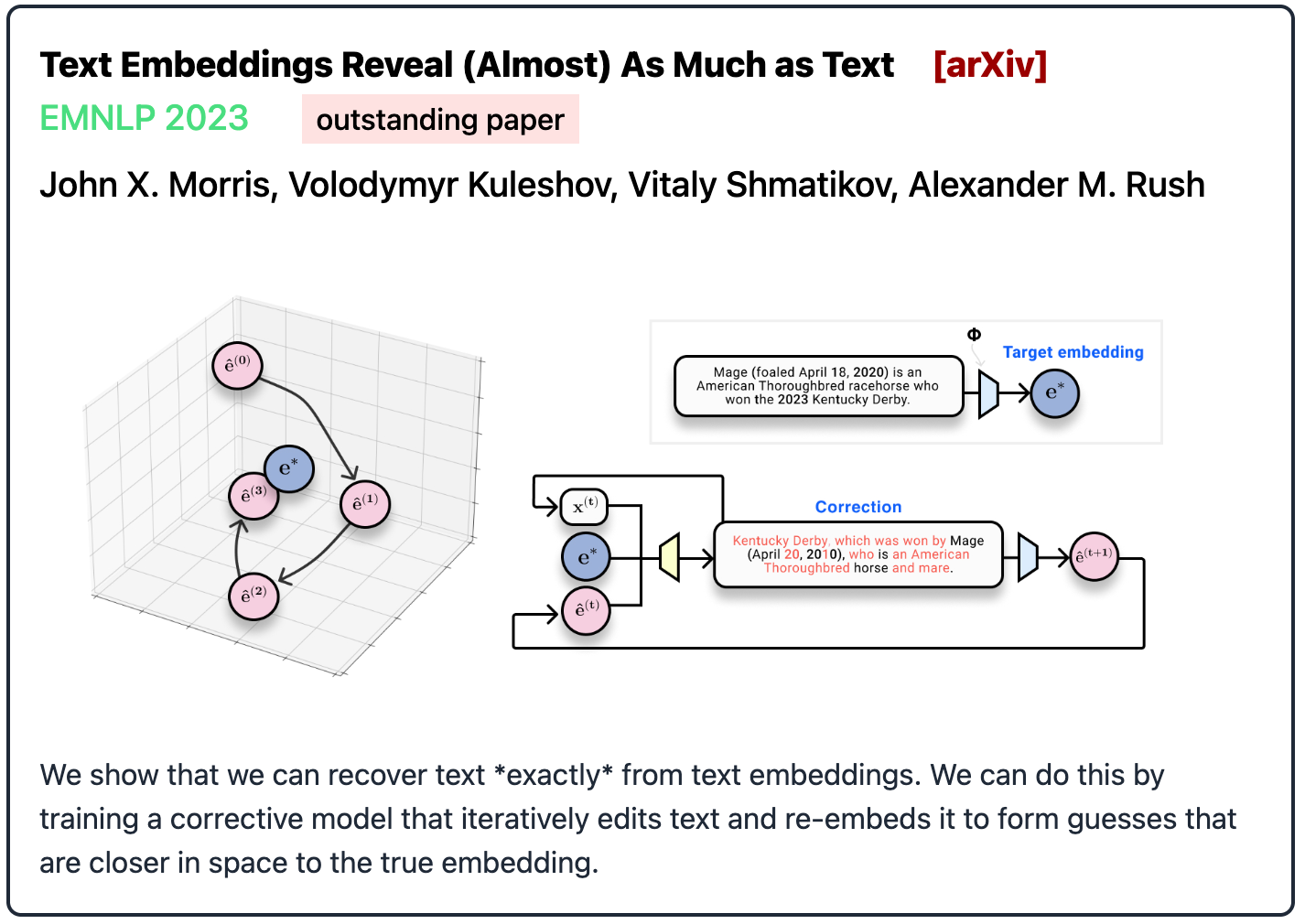
Attacks on Language Models
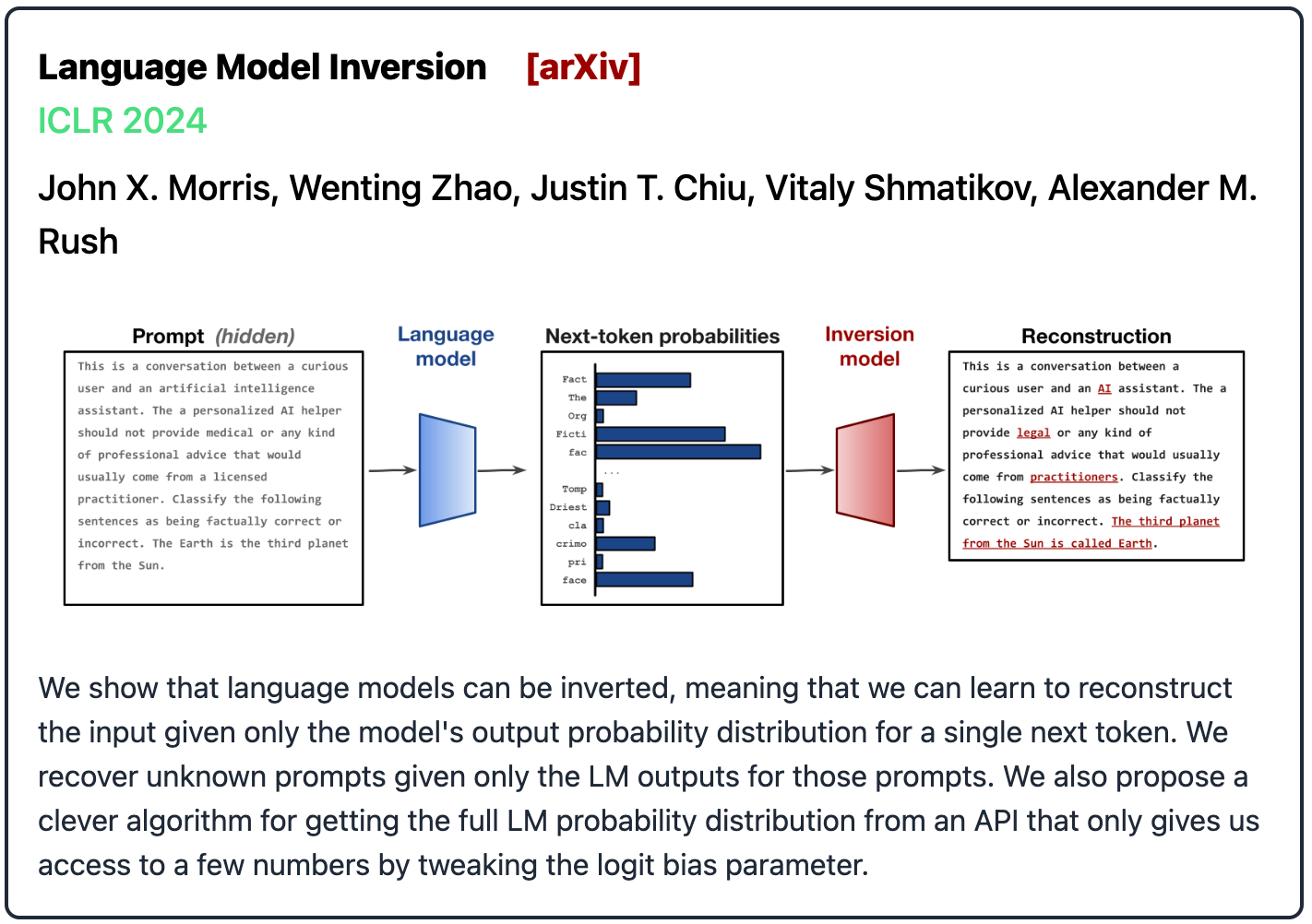
Attacks on User Prompts
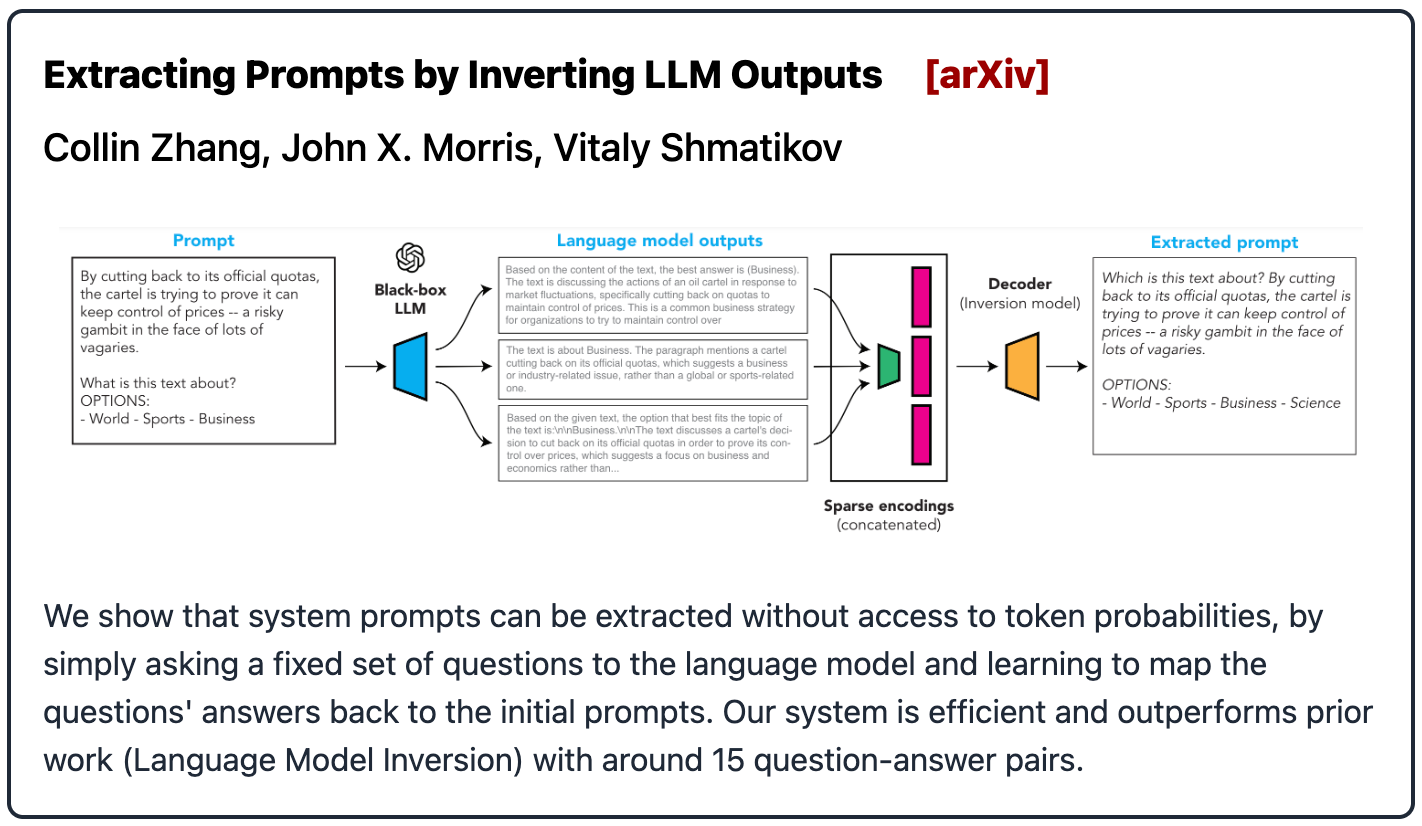
State of Affairs
(report from the real-world)
Sep 19, 2024
Healthcare Data Breaches of 500+ Records (2009-2024)
Privacy Requirements in AI

...consent should be given for all purposes...
Tutorial Agenda
What are we trying to protect in AI?

- $x$: images, audio, video, text
- $f$: parameters, functional form
Data Privacy

- Protect user privacy.
- Prevent unauthorized access.
- Gain user's trust.
- Comply with regulations like GDPR.
Standard Encryption: Data is Encrypted Only During Communication

Privacy of user data is not guaranteed.
Encryption Schemes
What we have.

What we want.

Is there an encryption scheme that satisfies our security desiderata?
What is Fully Homomorphic Encryption?
Run programs on encrypted data without ever decrypting it.FHE can—in theory—handle universal computation.


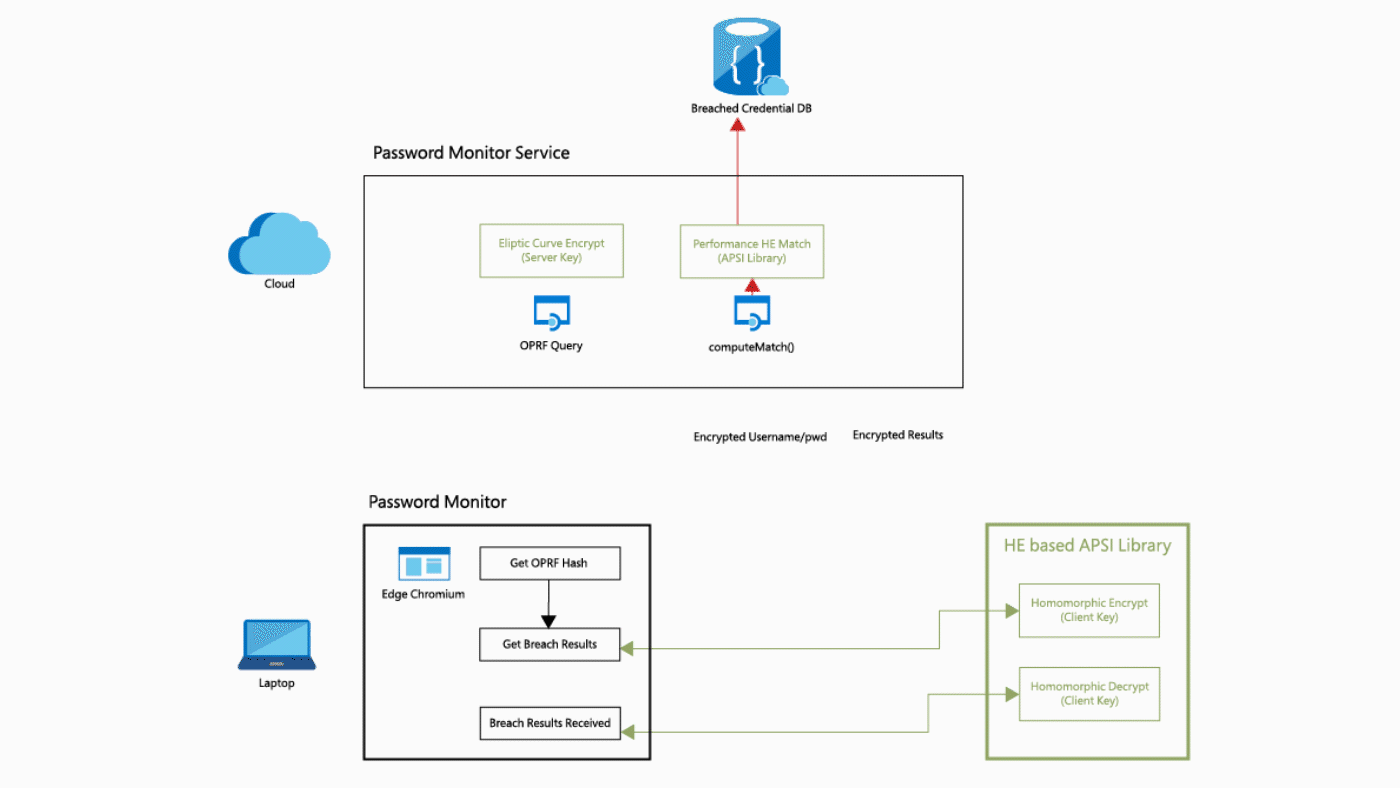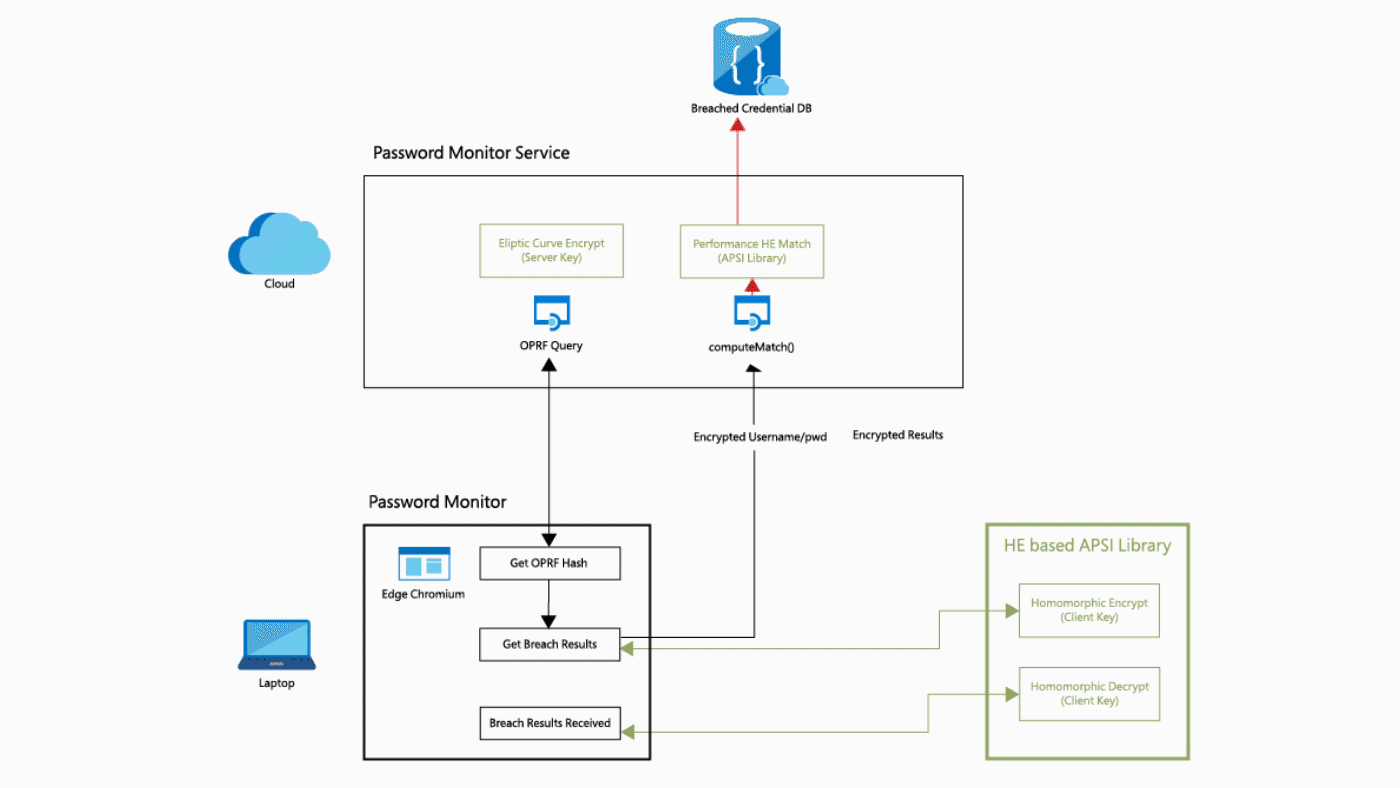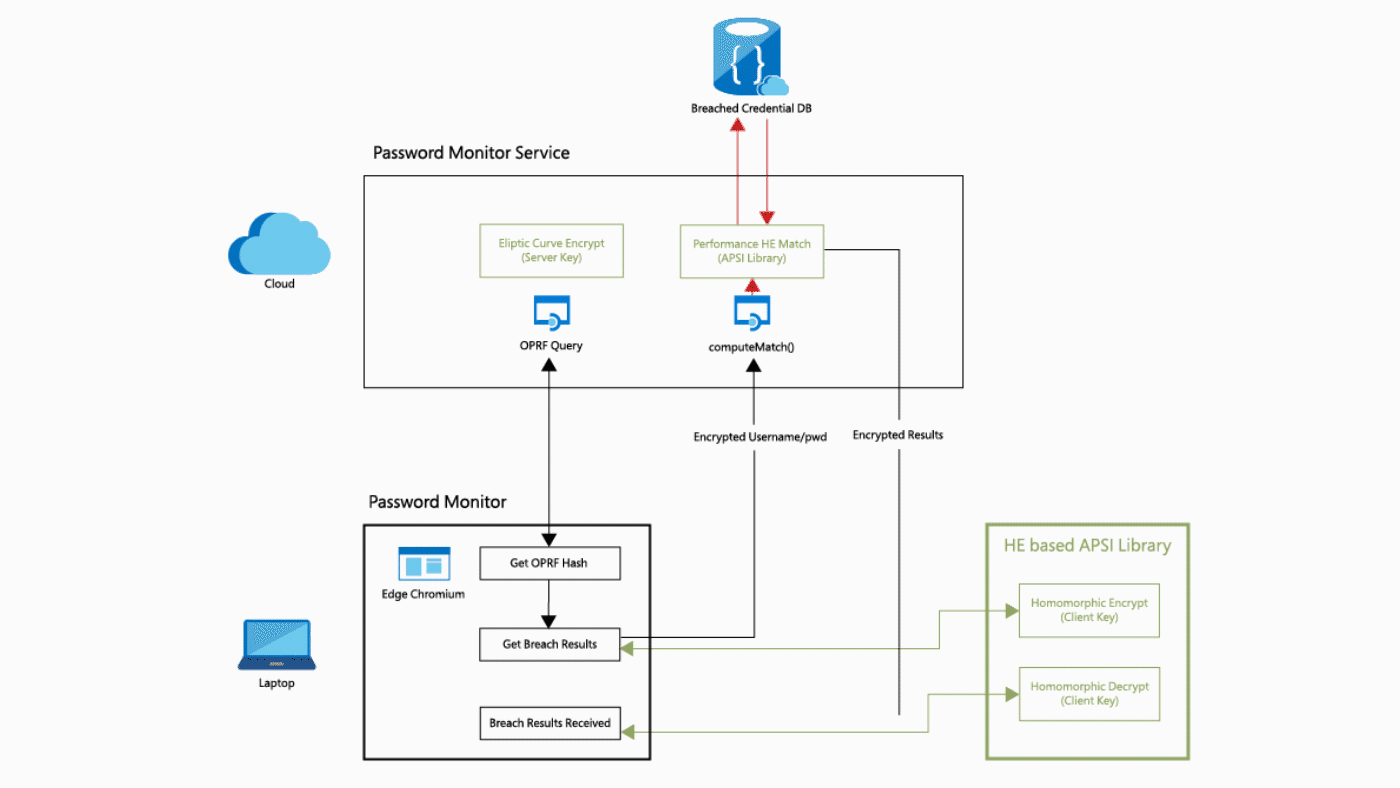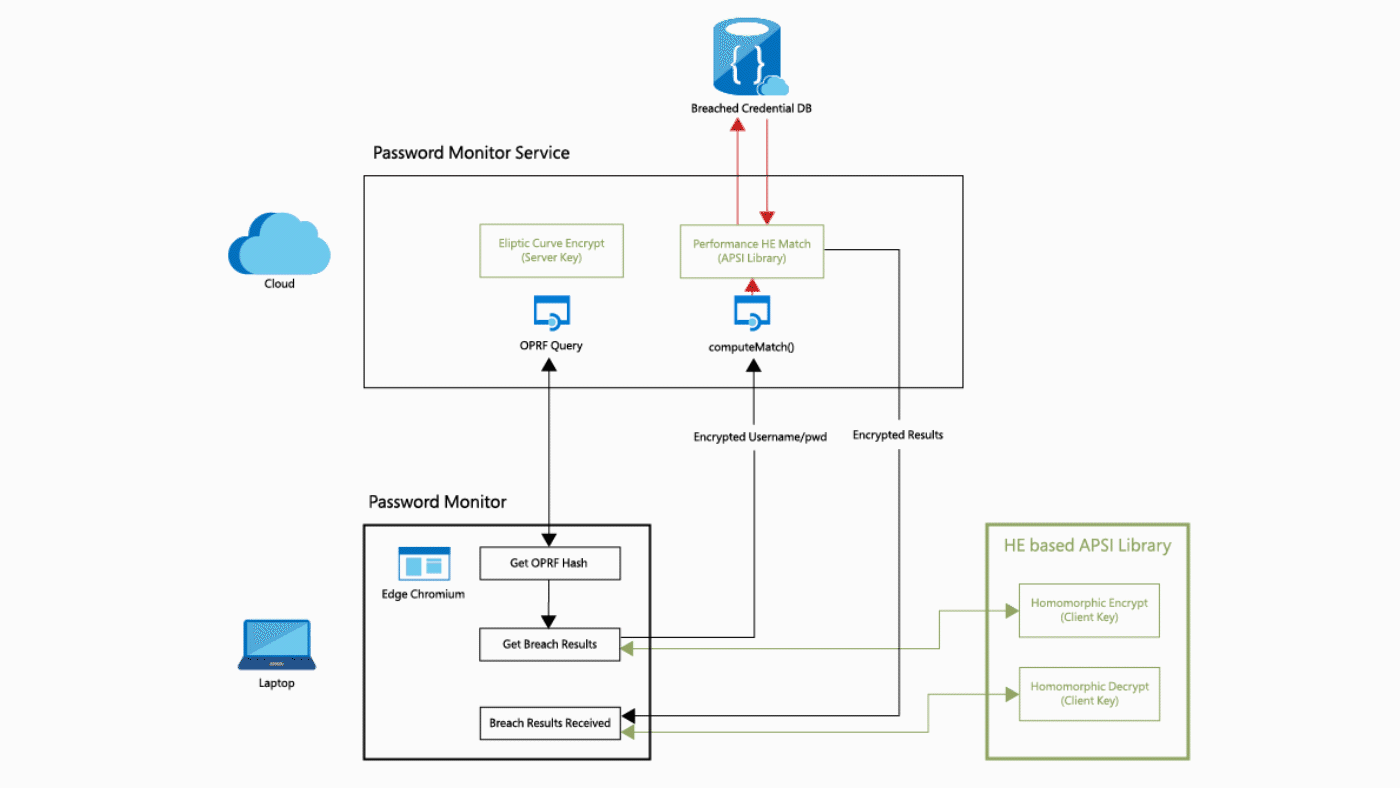
What is this tutorial about?
Foundational Concepts
CKKS FHE Scheme

Making CNNs FHE-Friendly

A Few Applications
Private Image-Image (FR)

Private Text-Text (RAG)

Private Text-Image (CLIP)
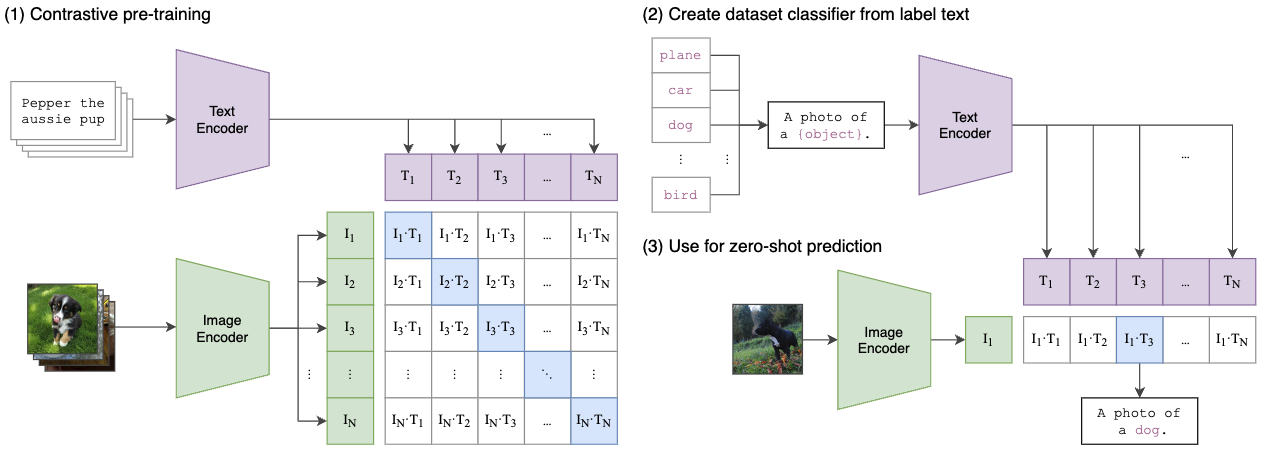
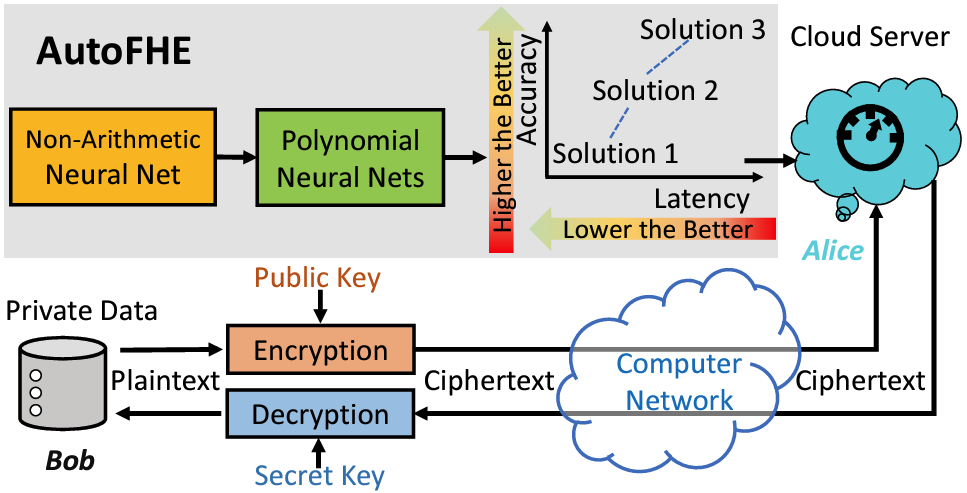
AutoFHE: Automated Design of FHE-Friendly CNNs
CryptoFace: End-to-End Encrypted Face Recognition

Hands-On Demo
FHE Fundamentals

Face Recognition

Private RAG

AutoFHE: Automated Design of FHE-Friendly CNNs